Keycloak as an Identity and Access Management System (IAM)
What Is IAM?
Identity and Access Management (IAM) is a critical discipline within IT and cybersecurity focused on managing digital identities and controlling user access to systems, applications, and data. IAM frameworks ensure that the right individuals have the appropriate access to technology resources, and only for the duration needed.
Keycloak serves as a modern and extensible IAM platform, enabling organizations to implement fine-grained access controls, centralized user management, and secure authentication flows—all while supporting open standards like OAuth 2.0, OpenID Connect, and SAML.
IAM Use Cases
Keycloak’s IAM capabilities are designed to meet the demands of enterprise-scale environments. Common IAM use cases include:
- Employee identity management across HR systems, internal portals, productivity tools, and custom applications
- Centralized authentication and authorization for developers, support, and operations teams across multiple applications
- Lifecycle management, including automated onboarding and offboarding processes
- Enforcing least-privilege access through role-based or attribute-based access controls
- Integrating with enterprise directories like LDAP or Microsoft Active Directory
These features help organizations maintain compliance, reduce risk, and increase operational efficiency.
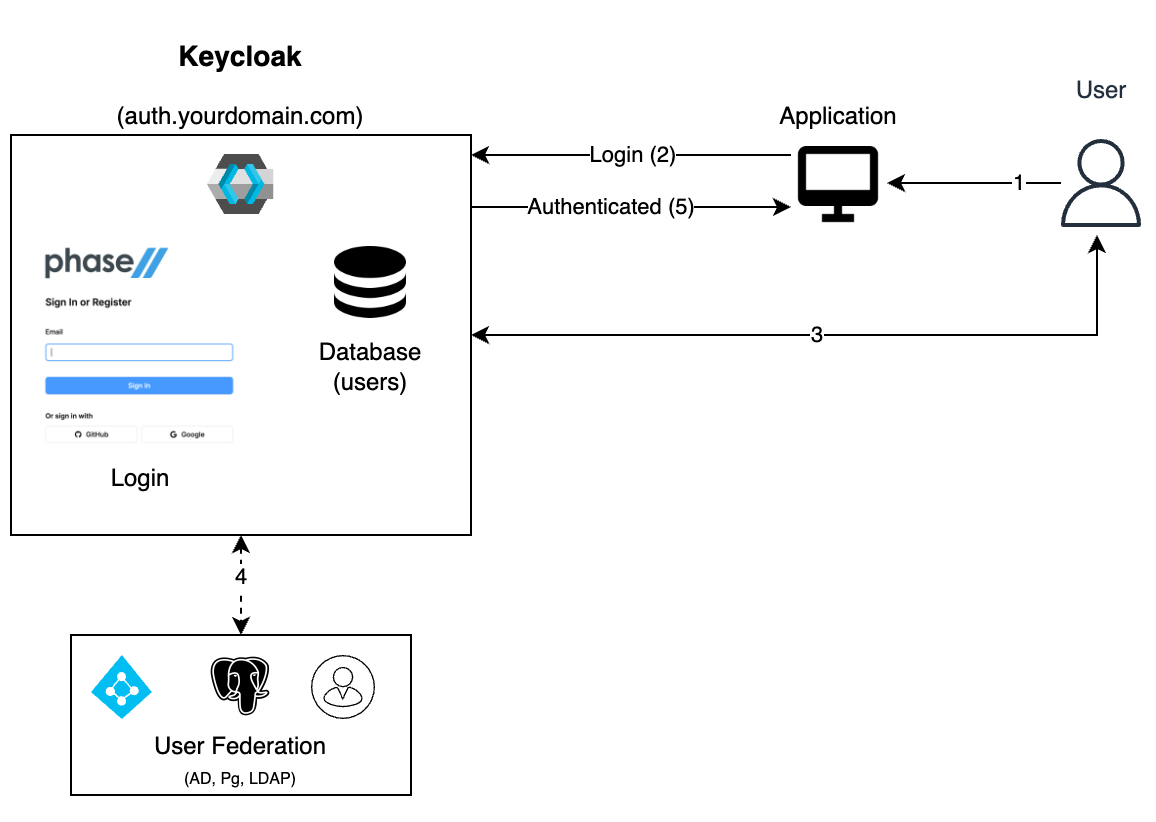
Why Keycloak for IAM?
Keycloak provides the core building blocks needed to implement a scalable, secure IAM system for internal users.
B2E Identity Management
Keycloak supports Business-to-Employee (B2E) scenarios where centralized identity management for staff and internal users is essential. It handles:
- Multi-application access through Single Sign-On (SSO)
- Secure credential handling and MFA
- Delegated admin functionality and role mapping
Centralized Access Control
Keycloak provides a single point of control for managing user roles, permissions, and policies across internal systems. This enables:
- Enforcement of consistent security policies across applications
- Reduced administrative overhead
- Improved visibility into who has access to what
Policy-Driven Authorization
Administrators can define policies based on:
- User roles and groups
- Resource types and scopes
- Custom logic via JavaScript or external permission services
Keycloak’s authorization features make it easier to implement least-privilege access models and zero trust architectures.
Integration with Enterprise Systems
Use Keycloak to federate identities from:
- LDAP directories
- Microsoft Active Directory
- Custom user databases
Keycloak also supports SCIM integrations and custom sync logic via its Service Provider Interfaces (SPIs). If you need SCIM, please reach out to support@phasetwo.io for assistance.
Developer-Friendly and Extensible
Whether you're building custom internal tools or integrating with SaaS providers, Keycloak supports:
- Standards-based authentication flows (OIDC, SAML)
- API-driven user management and auditing
- Custom authenticators, events, and login flows
Keycloak delivers IAM capabilities needed for enterprises looking to consolidate and simplify identity and access control. By leveraging Keycloak, organizations can secure internal applications, improve compliance, and streamline operations from a unified platform.